CYCRAFT
CYCRAFT AIR PLATFORM
How AIR Works
Either on premise or via cloud, AIR inspects thousands of endpoints simultaneously, detects real-time threats, discovers the root cause, and instantly responds. Our Xensor agent-less mode scans the endpoints on a daily scheduled basis, while the agent mode constantly monitors the endpoints for any malicious activities.
The collected raw report from Xensor is sent to CyCarrier (AI-powered forensic analytics center), where it investigates malware samples, commands in memory, and other suspicious activities that signatures-based or anti-virus fail to classify. To enrich the CyCarrier’s database, the Cybertotal (Threat Intelligence) platform integrates internal sources with updated multiple external CTI data sources to provide the unique business intelligence.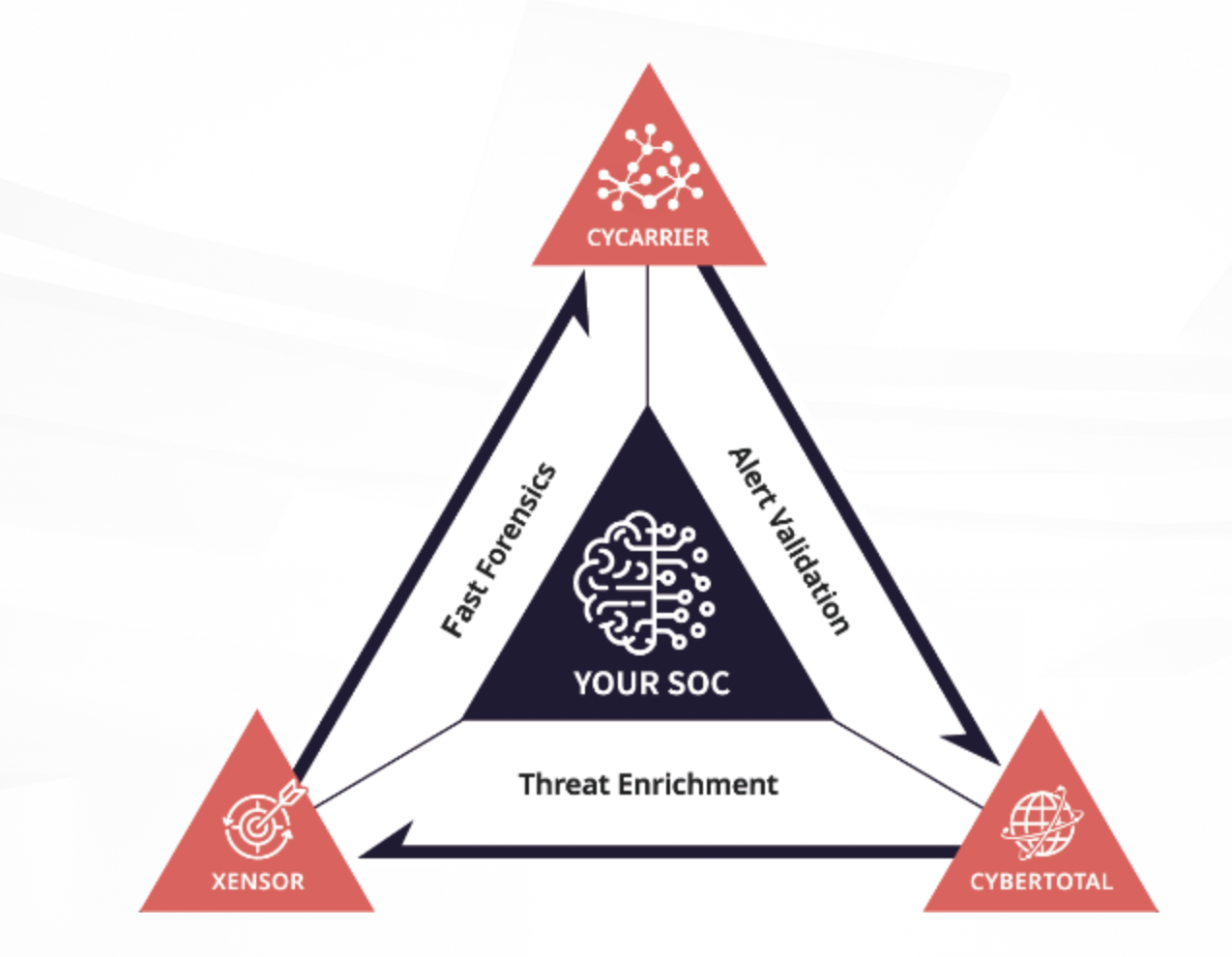
XENSOR
Combining machine learning with unique forensic telemetry technology, Xensor provides highly efficient automated threat triage and remote endpoint access for incident investigation and threat hunting.
An evolution above current security products, Xensor integrates multi-dimensional threat intelligence, including UEBA, program memory forensics, endpoint computer forensics, and network traffic analysis, without additional virus signatures or feature rules, to expediently respond and reduce security costs.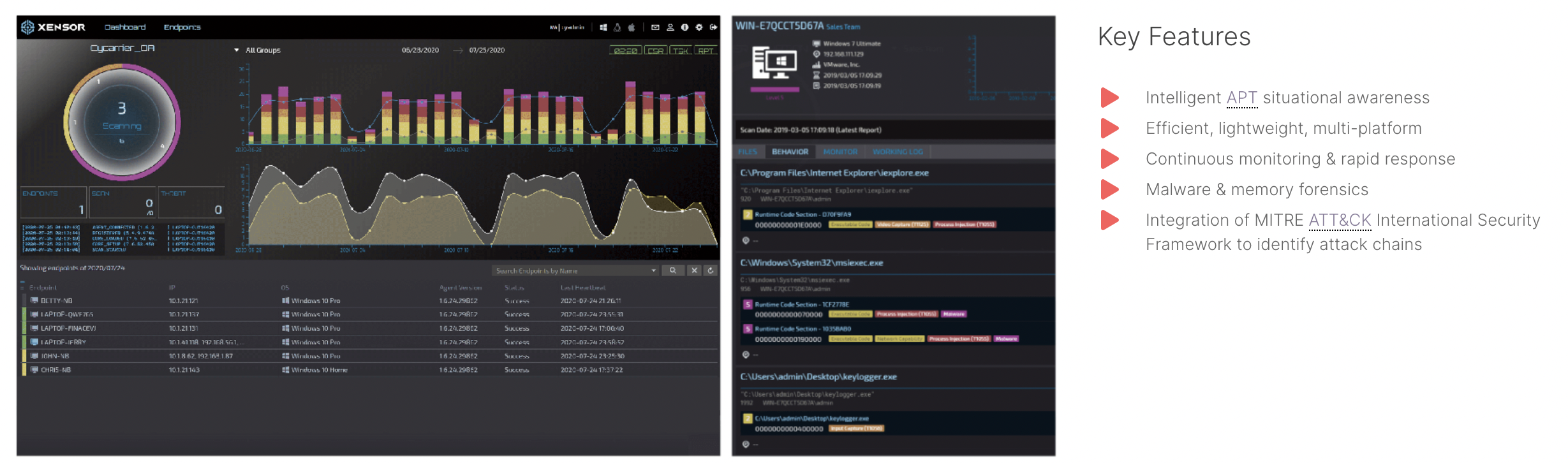
CYBERTOTAL
| Download CYBERTOTAL DataSheet |
Sharing threat intel and related security information has become an important early action mechanism to prevent and respond to attacks; however, traditional Cybersecurity Threat Intelligence (CTI) is dominated by exchanging static blacklists of IPs, domains, and MD5s, lacking higher-level attacker intelligence.
CyCraft’s Cyber Intel team has long tracked various forms of intrusion, provided historical information on APT groups, and brought together various global CTI sources of information* to provide high-quality threat intel and help companies quickly through AI automated correlation analysis and knowledge base optimization to identify threats and verify security alerts.
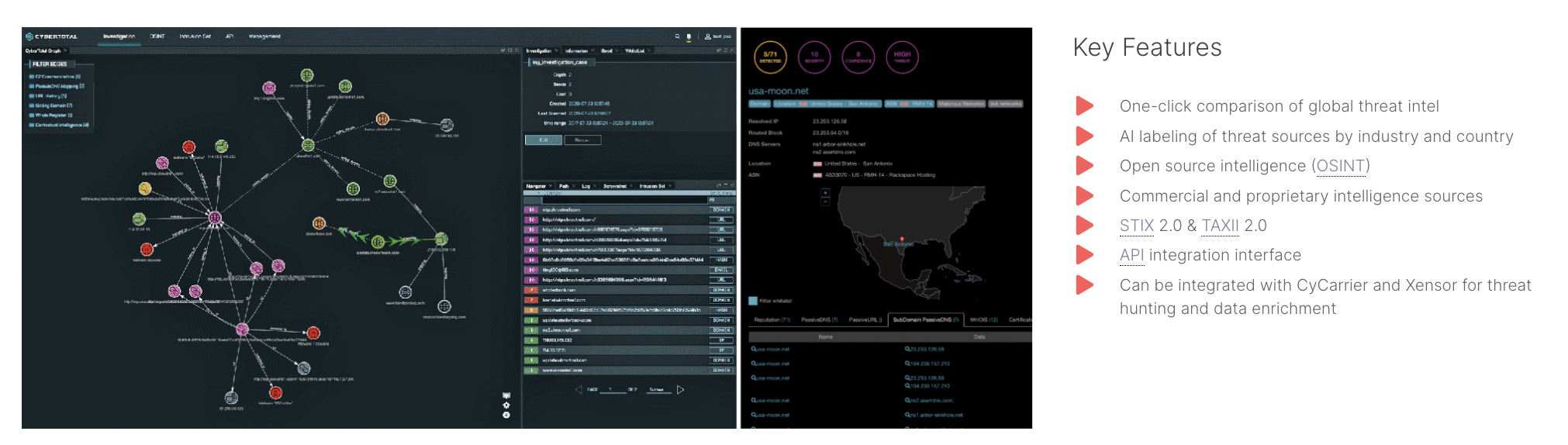
✔ CyberTotal provides a complete information security dictionary that supports 14 different threat indicator categories.
✔ CyberTotal provides STIX 2.0 reporting of the situation and supports TAXII to receive and push ISAC exchange information.
✔ CyberTotal provides a complete API integration interface to quickly integrate threat hunting and security.
- Enterprises can provide paid API keys to expand sources.